Security is not free
This was written a few days after the Crowdstrike incident but it has no relation to it.
Security isn’t free. Not for end users, open source maintainers, small companies, or big companies. We all pay one way or another to be more secure or to have the feeling of being more secure.
What a lot of folks don’t seem to understand is that most of the cost comes in one of the following forms:
I am going to focus a fair amount of this on time, specifically time spent on software dependency hell for security.
Money
Money is the most obvious, especially for people in charge of companies, or groups/divisions/organisations inside companies.
Even if you don’t need compliance with anything, you have to ensure the security of your assets, your customer assets, your employee assets, whether they are physical or digital.
You need tools, which add up to a fair amount. How many of us have looked at a Splunk bill and wanted to gouge our eyes out instead?
All of the above costs money, a lot of it. You need tooling and specialized people at a minimum. And when you don’t have one of those? It’s a matter of time - when something bad happens to you, it’s on you, no one else.
User Experience
This one is so complex, it’s hard to put into a simple post how user experiences change because of security.
I’d like to focus on the section about time so I’m going to provide a very simple example.
Multifactor authentication (MFA, 2FA included) makes the user experience worse. Much much worse.
It does make security better. Unless you’re using SMS. Then maybe it makes it worse as now a company somewhere will know your phone number and SMS can be intercepted.
And don’t get me started on backup codes. Just please don’t print them and leave the paper on the printer.
Anyway, my point here isn’t to advocate getting rid of MFA - please get yourself an Authenticator app and use MFA. The point is that it makes everything much more complex for users. As a side note, users will be glad to hear that it also makes everything more complex for the company to support MFA.
Security often times provides a worse user experience - more complexity, friction, (sometimes) worse performance, huge learning curve (try to explain MFA to your non-tech peeps).
The best products can do is get the right balance. Or as right as one can with what we have.
Time
This one is a lot hard to measure, specifically outside of organizations. I am going to use a very simple example of a package that I had to track down this weekend.
It all started with this alert in one of my repositories - for the purpose of the exercise here, ignore the fact that this doesn’t impact anything due to the way my project works.
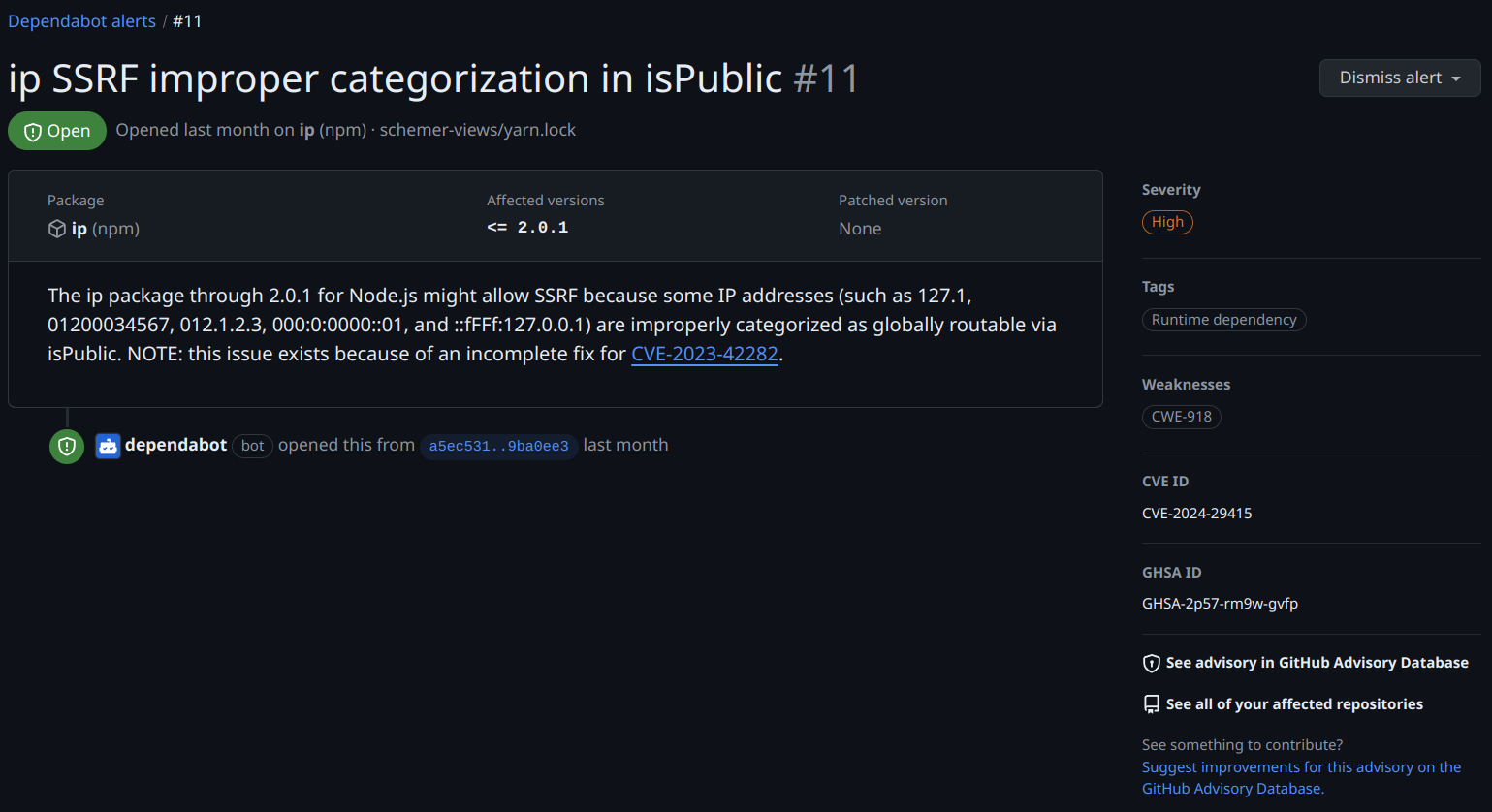
I went to npmjs and confirmed the version was at 2.0.1 and it was the latest.
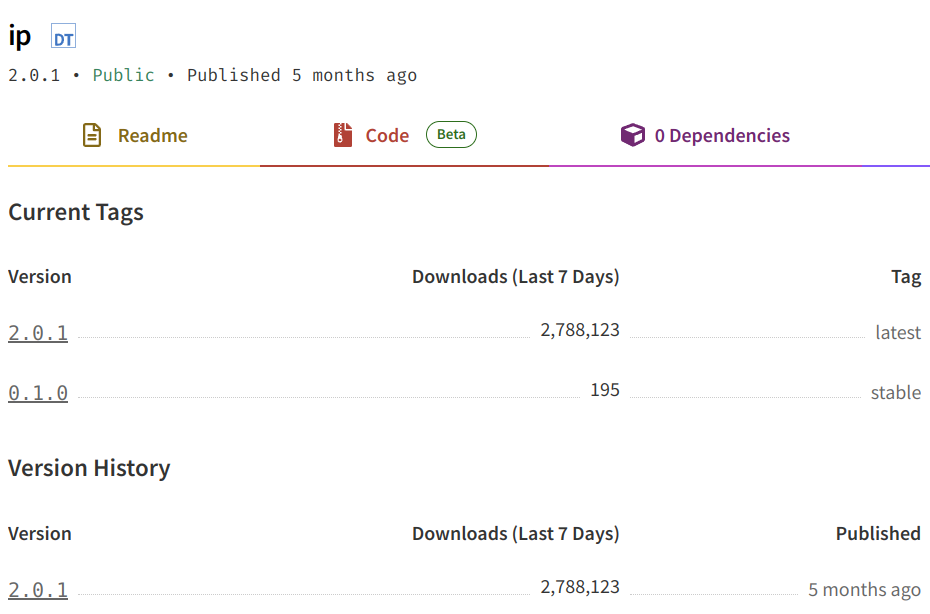
That put me on a path of finding which package depends on this one and so forth.
Easy enough with yarn why -R ip (the package that is at the top of the tree is not showing).
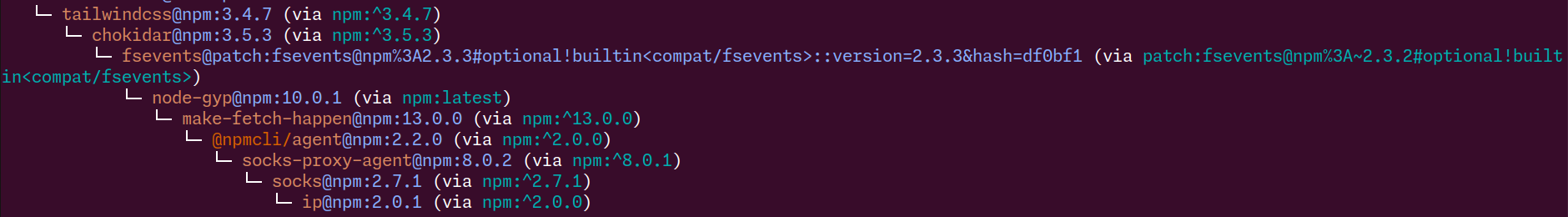
Alright, so is there an update for tailwindcss?
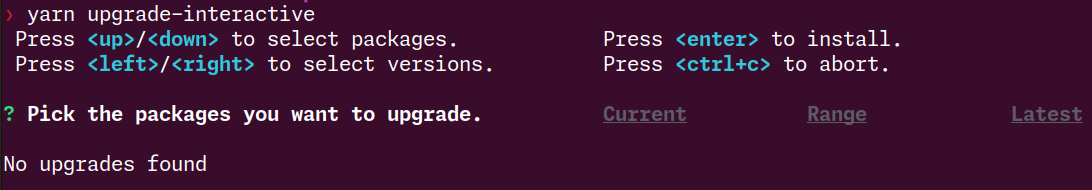
Well, that sucks.
I then moved to the next one in the tree: chokidar. Alternatively I could have done the opposite and go from the bottom (which I briefly did: socks had been updated a few months back to remove the ip dependency).
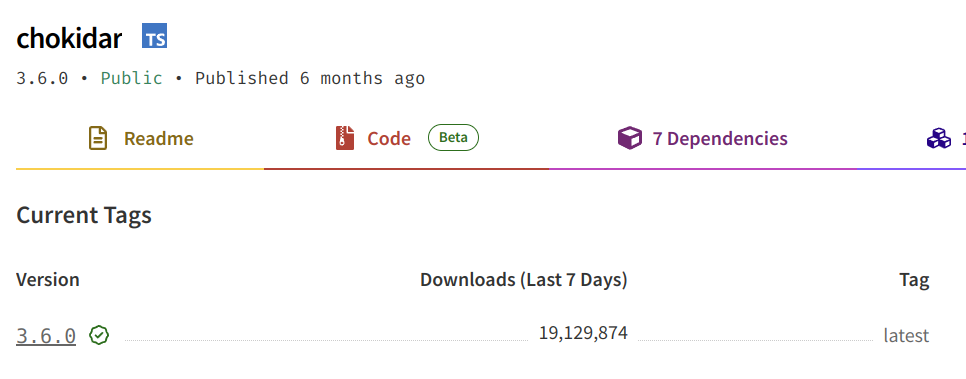
A bit depressing, that there’s a new version of chokidar out there (3.6.0) that tailwindcss hasn’t picked up on yet, even though it’s been out for 6 months. I didn’t investigate too deeply but my assumption is that it either is incompatible with other dependencies or the maintainers of tailwindcss struggle for time, as we all do).
This isn’t a critique of the ecosystem, or the maintainers of either project. It’s just that security needs time. Lots of it.
I finished by chucking this override and crossing my fingers that it would work (fortunately it did the trick) - I can’t see any side effects of this override.
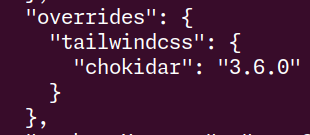
Running yarn why -R ip returns no results now.
Conclusion
Even if this whole ordeal took me less than 10 minutes to sort out, I kept being pulled into more questions and rabbit holes. "Should I open a ticket with tailwindcss? Should I instead just bump socks which has also fixed this and would arguably have a smaller surface area of potential side effects?"
And this is just one package. I haven’t even checked if the vulnerability is exploitable in my project. That would take a lot longer.
A lot of vulnerabilities reported aren’t even exploitable in most of the projects they are reported in. But you have to check. And that takes time.
Security isn’t free. It costs money, user experience, and time. And time is the most expensive of them all.
I am not advocating for not doing security. I am advocating for understanding the cost of security and making sure that you are willing to pay it.
And if you are not willing to pay it, then you are not willing to be secure.